GPS tracking is essential for securing trailers, RVs, and valuable equipment. But without encryption, your location data is vulnerable to interception and manipulation. Using the right encryption standards ensures your assets remain safe from theft, spoofing, and unauthorized access. Here are five key encryption methods to secure GPS tracking systems:
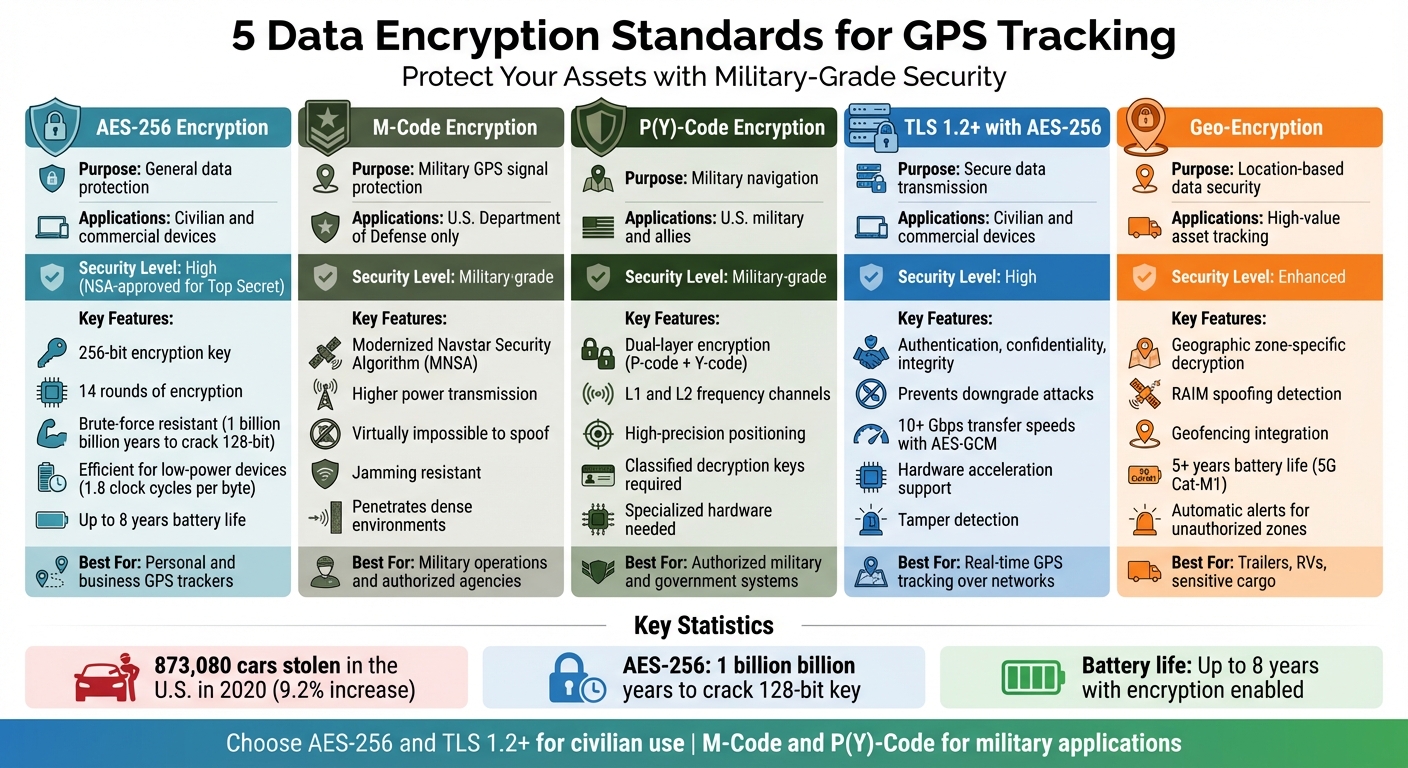
- AES-256 Encryption: A top-tier standard used for safeguarding sensitive data, including military-grade applications. It ensures data integrity and prevents brute-force attacks.
- M-Code Encryption: Exclusively for military use, this advanced GPS signal resists spoofing and jamming.
- P(Y)-Code Encryption: A dual-layer system for precise military navigation, offering high security against interception.
- TLS 1.2+ with AES-256: Protects data during transmission between GPS devices and servers, ensuring confidentiality and tamper-proof communication.
- Geo-Encryption: Adds location-based security by tying data decryption to specific geographic zones.
Quick Comparison
| Encryption Standard | Purpose | Applications | Key Features |
|---|---|---|---|
| AES-256 | General data protection | Civilian and commercial devices | High security, efficient for low-power devices |
| M-Code | Military GPS signal protection | U.S. Department of Defense | Spoofing/jamming resistance, high power |
| P(Y)-Code | Military navigation | U.S. military and allies | Dual-layer encryption, precise positioning |
| TLS 1.2+ with AES-256 | Secure data transmission | Civilian and commercial devices | Authentication, confidentiality, integrity |
| Geo-Encryption | Location-based data security | High-value asset tracking | Geographic zone-specific decryption |
Choose a GPS tracker with these encryption standards to protect your assets and ensure reliable performance. AES-256 and TLS 1.2+ are ideal for personal and business use, while M-Code and P(Y)-Code serve military needs. Geo-encryption adds an extra layer of safety for location-specific applications.
5 GPS Encryption Standards Comparison Chart
GPS Encrypted Military Signals M-code and Y-code – Spirent Federal
1. AES-256 Encryption
AES-256 is the benchmark for securing GPS tracking data. It’s the only publicly available cipher endorsed by the National Security Agency (NSA) for safeguarding "Top Secret" information. When your trailer GPS tracking system wirelessly transmits location data, AES-256 transforms that plain text into unreadable ciphertext using a 256-bit key and 14 rounds of encryption processes. This encryption forms the backbone of the security framework in GPS tracking devices.
Protection Against Interception and Spoofing
AES-256 encryption makes brute-force attacks virtually impossible. To put it into perspective, cracking a 128-bit AES key would take an estimated one billion billion years, and a 256-bit key is exponentially harder to break. When paired with Galois/Counter Mode (GCM), AES adds authentication and integrity checks. This ensures that your data remains untampered during transmission and prevents spoofing, verifying that location updates from hidden GPS trackers for trailers or other valuable assets are legitimate.
Applications in GPS Tracking Systems
In portable GPS trackers and wireless GPS tracker setups, AES-256 secures data exchanges between the tracking device and the server using TLS 1.2+ protocols. This safeguards real-time location updates, geofencing alerts, and playback of historical data. Additionally, it ensures that commands sent to the tracker – like disabling LED lights for covert use or adjusting reporting intervals – cannot be intercepted or manipulated.
Efficiency for Low-Power Devices
AES-256 is optimized for efficiency, even in compact GPS trackers with extended battery life. Designed for high speed and minimal RAM usage, the algorithm performs seamlessly on both low-power devices and high-performance systems. Thanks to AES-NI hardware acceleration in modern CPUs, encryption requires just about 1.8 clock cycles per byte. Advanced GPS trackers with power-saving features can deliver up to 8 years of battery life while maintaining encryption. This balance of security and efficiency is crucial for portable and wireless GPS trackers, ensuring long-lasting functionality without excessive energy consumption.
"The design and strength of all key lengths of the AES algorithm (i.e., 128, 192 and 256) are sufficient to protect classified information up to the SECRET level. TOP SECRET information will require use of either the 192 or 256 key lengths." – National Security Agency (NSA)
2. M-Code Encryption
M-Code is a specialized encryption standard designed to safeguard military GPS signals, granting access exclusively to the U.S. Department of Defense (DoD) and authorized agencies. This system ensures strong protection against threats like interception, jamming, and spoofing, thereby securing critical military operations. As an advanced step in GPS security, M-Code significantly strengthens the resilience of positioning and navigation systems. While it shares the high-security ethos of AES-256 encryption, M-Code is uniquely tailored for military use.
Security Against Interception and Spoofing
Traditional GPS signals lack encryption, making them vulnerable to malicious activities such as recording and rebroadcasting counterfeit signals. Spoofing attacks, for instance, use fake high-power signals to override legitimate ones, disrupting crucial functions like time synchronization and speed regulation. M-Code addresses these weaknesses by incorporating the Modernized Navstar Security Algorithm (MNSA), which makes spoofing nearly impossible. Additionally, it transmits at a higher power level, allowing signals to penetrate dense environments like forests and resist interference.
"The big advantage of the encrypted signal is that it is virtually impossible to spoof."
- John Fischer, Vice President for Advanced Research and Development, Orolia USA
Compatibility with Devices and Platforms
Because M-Code is specifically designed for military applications, it is limited to Military GPS User Equipment (M-GUE) and is not available for civilian GPS devices. Since 2017, all new U.S. military equipment must support M-Code, though some waivers have been granted during the transition to full adoption.
3. P(Y)-Code Encryption
P(Y)-Code is a highly secure GPS signal that combines the Precise (P) code with an additional classified Y-code layer. This dual-layer system ensures that only authorized users with the proper keys and hardware can access or decrypt the signal. It’s exclusively available to the United States military, select government agencies, and approved allied nations. This layered encryption not only safeguards the signal but also enhances its ability to resist interference and spoofing.
Security Against Interception and Spoofing
Unlike the civilian C/A code, P(Y)-Code encryption offers a much higher level of security, making it nearly impossible for adversaries to intercept or falsify the signal. The classified Y-code ensures that precise positioning data remains accessible only to receivers equipped with the necessary decryption keys. This level of protection is crucial for scenarios where the integrity of the signal must remain uncompromised.
Use Cases in GPS Tracking Systems
P(Y)-Code signals are broadcast on the L1 and L2 channels, offering high-precision navigation capabilities. While the U.S. government permits limited “codeless/semi-codeless” access for certain civilian applications, its primary role is to provide enhanced accuracy for authorized users. P(Y)-Code serves as an interim solution until the full deployment of newer signals like L2C and L5, as outlined in the Federal Radionavigation Plan (FRP).
Compatibility with Devices and Platforms
P(Y)-Code’s advanced encryption requires specialized hardware to decode the signal. The Interface Control Working Group (ICWG) oversees the technical specifications for GPS codes, including those for the L1 and L2 frequencies where P(Y)-Code operates with designated PRN codes. Due to these hardware requirements, P(Y)-Code is primarily used in authorized military and government systems. It is not designed for commercial GPS trackers or consumer devices like portable GPS units. While its usage is limited to specific applications, the encryption aligns with the rigorous standards seen in other high-security GPS tracking technologies.
sbb-itb-4827db2
4. TLS 1.2+ with AES-256
In GPS tracking devices, ensuring secure communication is a top priority. TLS 1.2+ (Transport Layer Security) establishes a protected channel between your GPS tracking device and its monitoring server using AES-256 encryption. This protocol safeguards data during transmission by ensuring authentication, confidentiality, and integrity. Its handshake process is designed to resist downgrade attacks, preventing attackers from forcing weaker security settings. This level of security is especially important for applications like hidden GPS trackers for trailers or portable devices.
Security Against Interception and Spoofing
TLS 1.2+ encryption ensures that location data remains secure while being transmitted. It encrypts the communication channel, making it nearly impossible for attackers to intercept or modify GPS coordinates. Any tampering attempts are detected, effectively preventing spoofing attacks.
"The primary goal of TLS is to provide a secure channel between two communicating peers… designed to prevent eavesdropping, tampering, and message forgery." – E. Rescorla, Editor of RFC 8446
Applications in GPS Tracking Systems
TLS 1.2+ with AES-256 encryption is a game-changer for GPS tracking systems, offering robust security for a variety of devices. This includes hidden GPS trackers for trailers, portable trackers, and wireless GPS trackers that rely on cellular or public networks. Whether used in trailer GPS tracking systems or fleet operations, this encryption ensures real-time location data remains private and tamper-proof.
This standard is particularly effective for trailer tracking, where maintaining security without draining battery life is critical. Modern implementations using AES-GCM (Galois/Counter Mode) provide data transfer speeds exceeding 10 gigabits per second, thanks to hardware acceleration. This means even compact GPS trackers with extended battery life can perform efficiently without compromising security.
Optimized for Resource-Constrained Devices
AES-GCM is specifically designed to work efficiently in resource-constrained devices like battery-powered GPS trackers. Through hardware pipelining, it achieves high-speed processing with minimal latency and energy consumption. For models like GPS trackers for trailers with no monthly fees, this efficiency is key – it ensures encryption doesn’t drain power unnecessarily, allowing the device to maintain strong security while preserving battery life.
"AES-GCM is not only efficient and secure, but hardware implementations can achieve high speeds with low cost and low latency, because the mode can be pipelined." – J. Salowey, Cisco Systems, Inc.
5. Geo-Encryption
Geo-encryption steps up location-based security by ensuring that tracking data can only be accessed or decrypted within specific geographic zones. This is especially useful for trailer GPS tracking systems and portable GPS trackers, where risks like unauthorized access or signal tampering can lead to major problems. Since standard GPS signals are open and unencrypted, they’re susceptible to spoofing attacks – where hackers send fake position, navigation, or time data to mislead systems. By tying decryption to specific locations, geo-encryption adds a crucial layer of defense, enhancing the reliability of GPS tracking systems.
Security Against Interception and Spoofing
Geo-encryption works alongside traditional encryption, but with an added twist: it ties decryption to specific geographic areas. Advanced systems often use Receiver Autonomous Integrity Monitoring (RAIM) to detect spoofing attempts by identifying irregularities in satellite signals. If a device moves outside its authorized zone, it triggers immediate alerts. This feature is particularly effective against carry-off attacks, where receivers are slowly moved out of their intended range without detection.
A striking example occurred in September 2023, when a flight traveling from Europe to Qatar encountered severe GNSS spoofing over Iraqi airspace. The aircraft lost its GPS sensors, and its Inertia Reference System revealed it had drifted 80 miles off course. Meanwhile, avionics falsely reported a ground speed of 0 MPH. The crew had to rely on alternate navigation methods to complete the journey.
Use Cases in GPS Tracking Systems
Geo-encryption is invaluable for protecting high-value assets like trailers, RVs, and sensitive cargo. For wireless GPS trackers monitoring critical shipments, this technology ensures that telematics and location data stay secure, even if a trailer veers off its designated route. Some high-security trackers are designed to "sleep" when stationary, making them harder to detect by RF scanners used by thieves to locate tracking devices. Combining geo-encryption with geofencing allows operators to establish "safe zones." Any movement outside these zones triggers instant alerts, signaling potential tampering or theft.
One example comes from a construction company that adopted a fleet management solution using mini IoT tags and hybrid trackers. These tools secured high-value equipment and trailers across multiple job sites. By implementing real-time tracking with location-based security, the company not only reduced tool theft but also improved asset utilization, leading to increased profitability. This approach integrates seamlessly with existing encryption standards, further bolstering GPS tracking security.
Efficiency in Resource-Constrained Environments
Modern geo-encrypted devices leverage 5G Cat-M1 technology, enabling battery-powered trackers to operate for up to five years without needing maintenance. These devices use efficient algorithms like AES-256, which safeguard electronic data without draining battery life unnecessarily. Some specialized trackers also monitor additional satellites to maintain strong reception, even in challenging environments. This makes geo-encryption a practical solution for GPS trackers designed to last longer while maintaining robust functionality.
How These Standards Work in GPS Tracking Devices
Modern portable GPS trackers are designed to keep your data secure by encrypting information at multiple points: from the satellite to the receiver, from the tracker to the server, and finally, from the server to your mobile app.
Battery-powered trackers, like those used for trailer monitoring, rely on AES-256-CCM encryption for device-to-server communication. This level of encryption is considered highly secure and has the added benefit of being energy-efficient, which is crucial for devices that need to function for years without maintenance. AES-256 encryption is essentially impossible to break, offering a strong layer of security across all communication channels.
The protection doesn’t stop there. When you check your tracker through a mobile app, the connection is secured with HTTPS using TLS 1.2+ and SHA-256 encryption. This setup helps block man-in-the-middle attacks. For Bluetooth-enabled configurations, AES-128 encryption secures the short-range connection between your smartphone and the tracker.
These advanced encryption methods are key to the reliable performance of Piritiz GPS trackers. In addition to robust security, these devices are built for efficiency, offering up to 5 years of battery life thanks to smart energy management. Each tracker is available for $19.95, with subscription plans starting at $7.00 per month.
"AES-GCM is not only efficient and secure, but hardware implementations can achieve high speeds with low cost and low latency, because the mode can be pipelined." – IETF RFC 5288
To further enhance security, each tracker uses unique, randomly generated encryption keys and Message Authentication Codes (MAC) to verify the authenticity of both the device and the server. This method ensures that even if one device in your fleet were compromised, the others would remain secure with their own encryption credentials, effectively preventing spoofing attacks.
Conclusion
The five encryption standards discussed – AES-256, M-Code, P(Y)-Code, TLS 1.2+ with AES-256, and Geo-Encryption – provide robust, multi-layered protection for GPS tracking data. Encryption safeguards against spoofing, transmission security ensures data isn’t intercepted, and storage protection keeps location history secure. These layers of protection are essential, particularly when you consider that in 2020 alone, 873,080 cars were stolen in the United States – a 9.2% jump from the previous year.
When selecting a GPS tracker, prioritize one with strong encryption like AES-256, the federal standard for safeguarding sensitive information. As Elaine B. Barker from NIST explains:
"This document is intended to provide guidance to the Federal Government for using cryptography and NIST’s cryptographic standards to protect sensitive, but unclassified digitized information during transmission and while in storage."
Standard factory equipment often lacks adequate security, making it easy for thieves to disable unencrypted alarms in seconds. This highlights the importance of choosing GPS trackers – whether for trailers or other assets – that meet NIST-approved encryption standards. A hidden GPS tracker for trailer or a GPS tracker for trailer with no monthly fee equipped with these protections can be a critical line of defense.
For those seeking a small GPS tracker with long battery life or a trailer GPS tracking system, ensure the device uses AES-256 or TLS 1.2+ encryption. These standards make intercepted data unreadable, offering around-the-clock protection for your assets.
FAQs
Why is AES-256 encryption ideal for both civilian and military GPS tracking systems?
AES-256 stands out as a powerful encryption standard, recognized and approved by the National Institute of Standards and Technology (NIST). With its 256-bit key, it generates an immense key space, making it nearly impossible to crack. This unmatched level of protection makes it ideal for military-grade GPS tracking systems, where defending against cyber threats is critical.
What’s impressive is that AES-256 doesn’t sacrifice performance for security. It’s designed to be computationally efficient, which is why it’s also widely used in civilian GPS tracking applications. From trailer GPS trackers to portable devices, it provides a reliable layer of security. This combination of strength and efficiency has cemented AES-256 as a go-to solution for protecting sensitive data across both high-security and everyday uses.
How does geo-encryption improve the security of GPS tracking systems?
Geo-encryption boosts the security of GPS tracking by encrypting location data, ensuring that only those with the correct cryptographic key can access it. When a GPS tracker transmits coordinates, secure protocols like SSL/TLS protect the data during transmission, preventing interception or unauthorized access. Once the data reaches its destination, it’s stored using advanced encryption methods such as AES-256, which keeps it unreadable without the proper decryption key.
This dual-layer encryption – covering both transmission and storage – provides a strong shield for sensitive location data. It blocks unauthorized tracking, safeguards user privacy, and helps comply with data protection regulations. For trailer GPS tracking systems, hidden trackers, and portable wireless devices, this level of security ensures users can rely on their systems with confidence.
Why is using TLS 1.2+ with AES-256 crucial for securing GPS tracking data?
When it comes to securing GPS tracking data, TLS 1.2+ paired with AES-256 encryption is a must. This setup uses a highly secure protocol along with a 256-bit symmetric key to encrypt information, ensuring that the data stays private and protected from interception or tampering during transmission.
AES-256 delivers strong encryption that’s resistant to brute-force attacks, while TLS 1.2+ aligns with modern security standards to maintain compatibility. This powerful combination is crucial for safeguarding sensitive GPS data, whether it’s for trailer GPS tracking systems or portable wireless GPS trackers.






